A Behind the Scenes Look at How the TrustPoint Team Keeps our Tech Secure
Near Field Communication, Internet of Things and Vehicle-to-Vehicle — these are all emerging technologies that promise to improve our lives. Without the proper security, they can also leave us vulnerable to hacks and attacks.
The TrustPoint team spends their days ensuring the security of these complex systems. Recently, four of our crypto experts, Dr. Robert Lambert (VP Product Development), Jay Gallant (Software Developer), Dr. Nevine Ebeid (Senior Embedded Security System Engineer) and Tony Rosati (VP of NFC Business Development), shared why they’ve dedicated their education and careers to keeping one step ahead of the hackers.
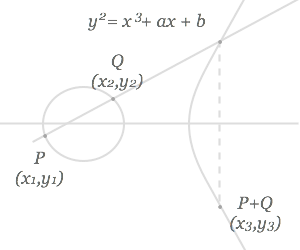
In a newly published paper, How the TrustPoint Team Keeps our Tech Secure, each shares their insight into their specific area of expertise. They provide a concise explanation of the basics of NFC, IoT and V2V, and explore the merits of using Elliptic Curve Cryptography (ECC) and the potential it offers because of its highly secure nature and extremely efficient size.
Click here to request a copy of the full interview to gain a better understanding of the technology we protect and a glimpse at the security we’re dedicated to providing.
