Counterfeit Wines, A Multi Billion Dollar Problem

Counterfeit wines made headlines in the world of rare wine collecting with two fascinating stories. The first story is the New Yorker’s …

Counterfeit wines made headlines in the world of rare wine collecting with two fascinating stories. The first story is the New Yorker’s …
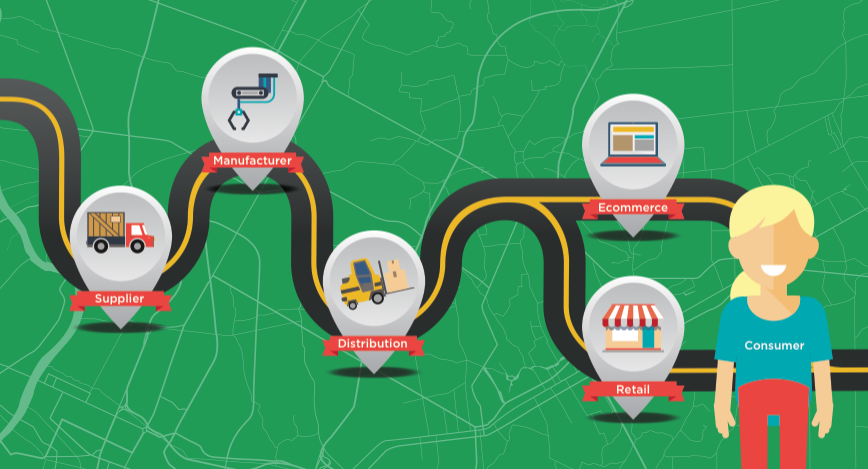
Intermediaries refer to all parties in the supply chain. They include raw material suppliers, manufacturers, distributors, shipping companies, …
The most common use for NFC technology is to turn a smartphone into a digital wallet. It can collect and store the data from credit and debit cards …
Taylor Swift has long held a passionate stance on the protection of intellectual property in the music industry, and is not afraid to stand up for …
The options for using NFC tags in advertising are endless. NFC (or near field communication) is a wireless technology that facilitates fast and efficient …
BlackSeal currently requires NFC tags with about 500 bytes of memory available to be able to fit a URL plus a signature on the tag. But is it possible …
Despite efforts to combat counterfeits, Alibaba ecommerce websites reportedly “encourage, assist” fake merchandise.

In this post we compare two technologies: NFC tags and the well-established QR codes.

NFC tags can be used in a wide variety of ways to help make your life easier.
Understanding the customer’s behaviour is key to the success for most manufacturers. Billions have been spent in research. Countless hours have gone …
In 2013 the World Customs Organization (WCO) said, “Counterfeit goods account for nearly 10 percent of worldwide trade, an estimated $500 billion …
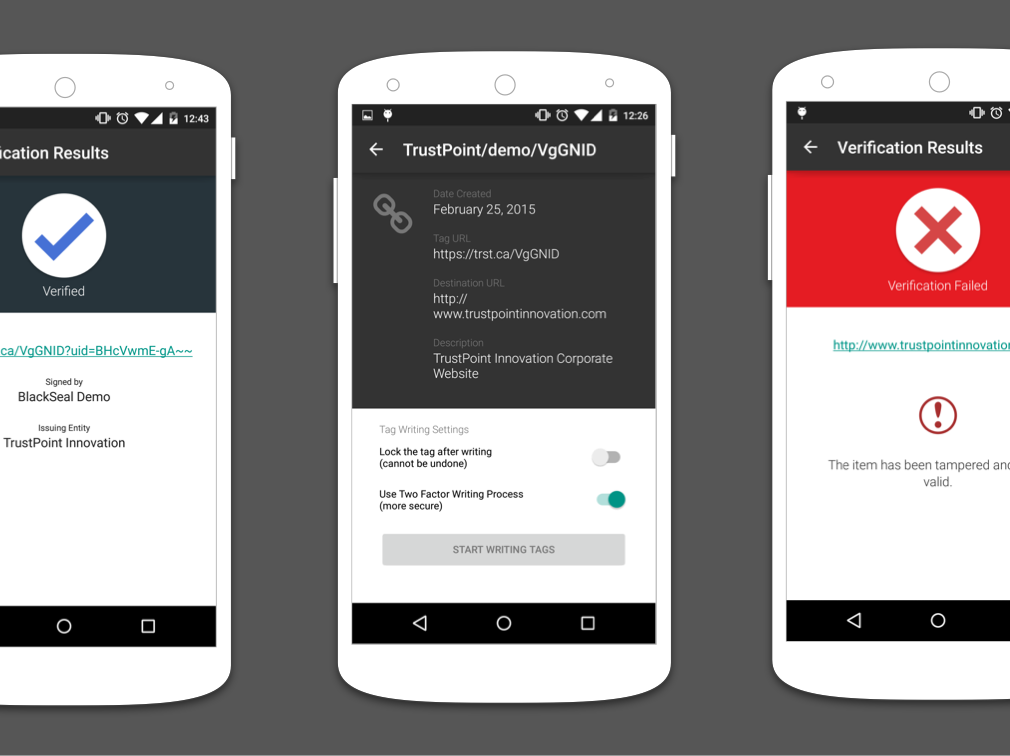
Yesterday we announced the release of BlackSeal. Included with the release is the BlackSeal app. This post discusses the app’s unique security features.

Today we are announcing BlackSeal, a new type of authenticity service. It solves the problem of adding provable authenticity to physical products.

In a recent CTV W5 Episode investigators highlight the extent of counterfeit goods in apparel, memorabilia and event ticket markets. They highlight a …
NFC tags are being used to build and strengthen products in a number of creative ways. Here are three that are top of mind at TrustPoint Innovation…
NFC security is highly dependant on the targeted application and mode of operation. This post explores the three modes of NFC: Tag Reader/Writer, Card …
This question was posted a few years ago by Eric Vétillard in this blog post.
Most smart phones (sans the iPhone) are NFC enabled out of the box and can read NFC tags without installing any apps. Naturally early adopters will want …